Research Highlights
 |
 |
 |
Secure and Fair Spectrum Sharing |
Privacy-preserving Communications |
PHY-layer Security |
 |
 |
 |
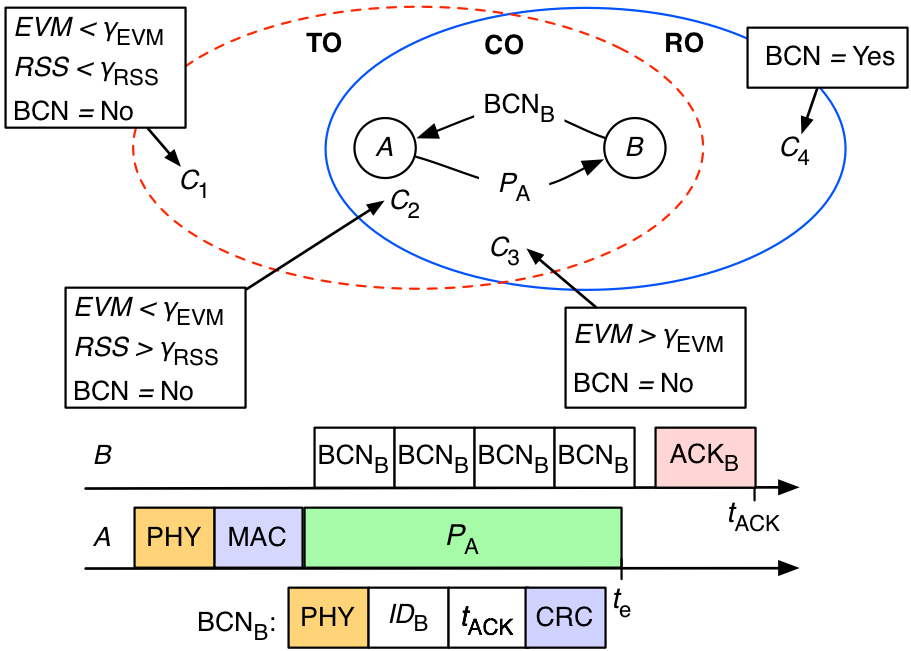
Secure Channel Access |
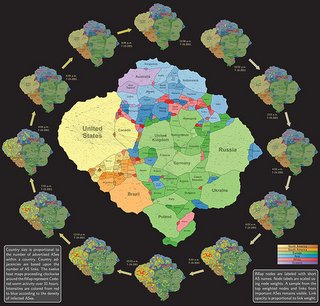
Cyber-Social Security Models |
iMaps |
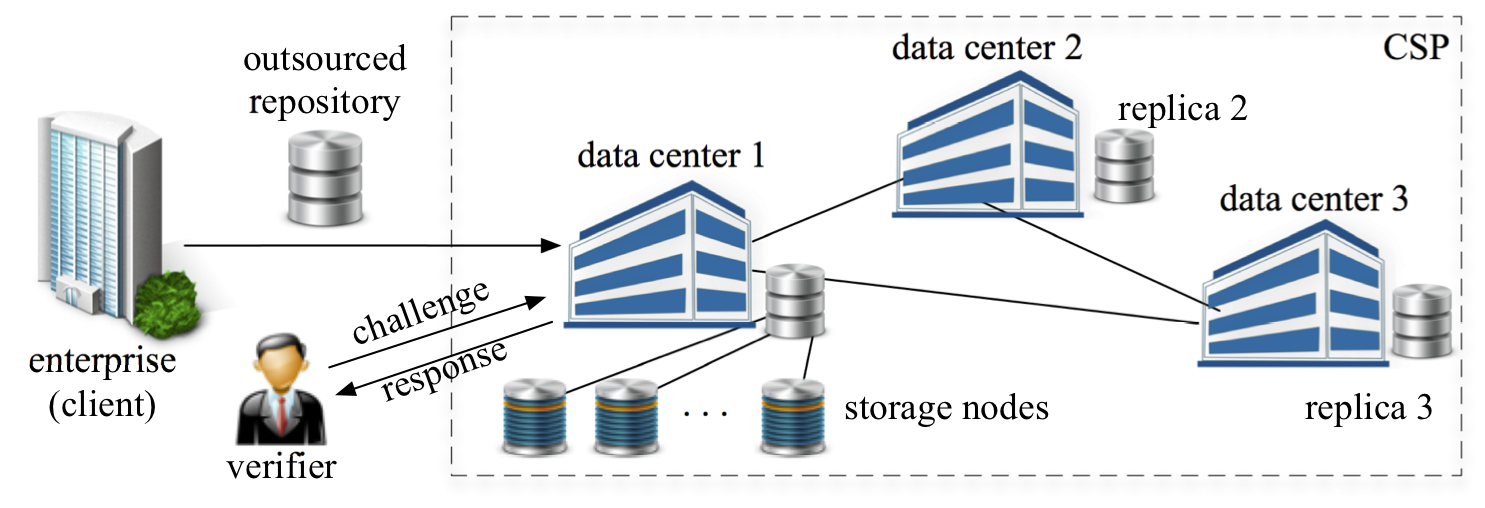 |
Cloud Storage Verification |