|
The open nature of the wireless medium leaves it exposed to adversarial eavesdroppers. Using
commodity radio hardware, unauthorized adversaries can easily intercept packet transmissions. Although encryption can be applied to ensure information secrecy, eavesdroppers can still perform low-level RF and traffic analysis, and capture with different degrees of certainty several communication attributes, such as the packet size, its duration, inter-packet times, traffic directionality, channel state information, etc. Through knowledge of the protocol functionality, these attributes can be correlated to create transmission “fingerprints”, from which an adversary can derive a wealth of contextual information, including the relative significance and locations of the communicating parties, their mobility patterns, the applications they run, their visited web-sites, etc. Contextual information can subsequently be used to launch sophisticated attacks (e.g., selective jamming/dropping, targeted node compromise, intelligent DoS attacks, etc.). State-of-the-art privacy research focuses on the leakage of high-layer attributes, typically captured from unencrypted headers. In fact, most efforts in this domain deal with demonstrating the feasibility of privacy attacks, and less with providing remedies. Countermeasures are often limited to specific “point” attacks, without addressing their root cause, i.e., the exposure of transmission signatures.
In this project, we aim at advancing the state-of the-art on signature-free secure
wireless communications. Our techniques are meant to counter different time scales of eavesdropping.
For short-term eavesdropping, we are developing novel PHY-layer techniques for concealing transmission
attributes. These techniques exploit advances in MIMO and self-interference suppression to provide
integrated transmitter/receiver friendly jamming, with the goal of preventing eavesdropping
irrespective of the eavesdropper's location. Novel digital/analog signal combining schemes are also
used to create to obfuscate additional fingerprints. For longer time-scale and/or colluding eavesdroppers,
we are developing randomization techniques that aim at countering traffic and frequency inference
attacks facilitated by long-term monitoring of transmission activities over several links.
 |
 |
| (a) |
(b) |
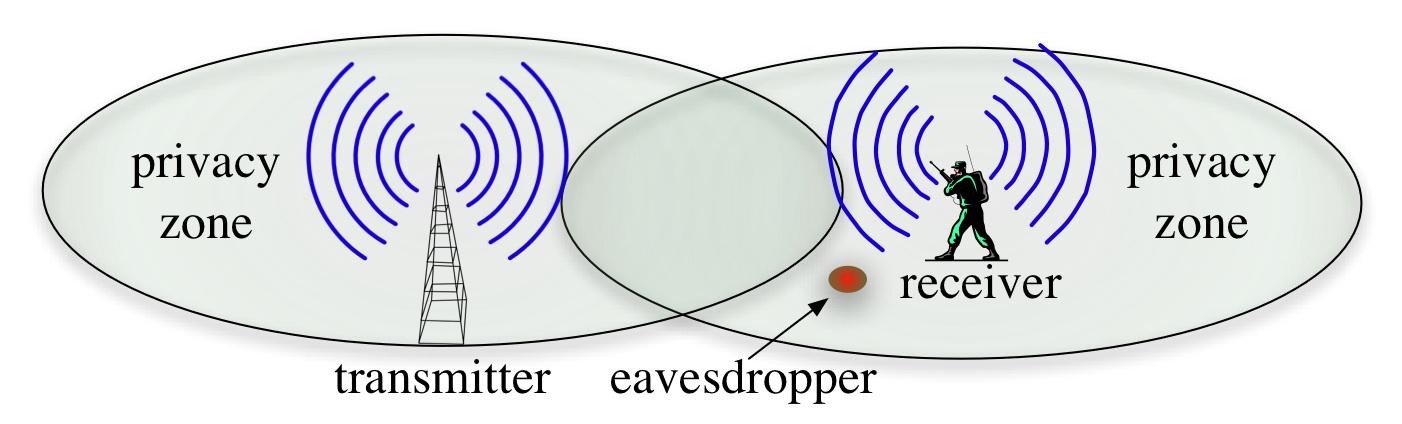
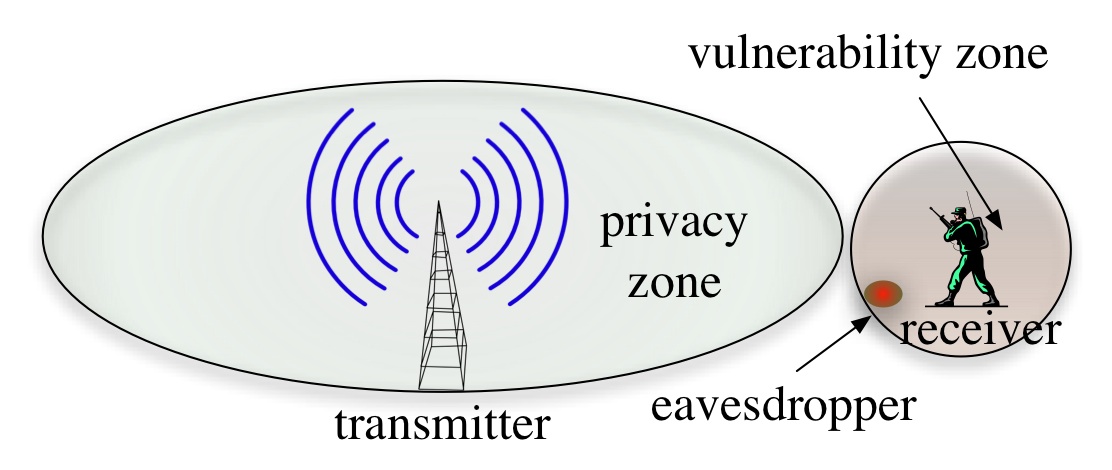
(a) Transmitter injects artificial noise to create a privacy zone.
A vulnerability zone is created around the receiver. An eavesdropper in
close proximity to the receiver can decode transmitted packets. (b) proposed system:
both the transmitter and the receiver inject artificial noise in order to extend the
privacy zone to any possible eavesdropper location. The receiver uses self-interference
suppression techniques to decode the packets sent by the transmitter.
|
|